Read More: How to Create an Affiliate Marketing Website
The technique of defending computers, servers, mobile devices, electronic systems, networks, and data from online attacks, theft, and destruction is known as computer security, also referred to as cybersecurity. Computer security is more crucial than ever in today’s world of increased connectivity. The risk of cyber attacks is increasing as more and more personal and business information is being stored and exchanged electronically.

People and organizations need to be aware of the various kinds of threats to computer security. These consist of:
Malicious software such as viruses and malware can harm or steal data from a computer. They typically spread via websites, social media, and email attachments.
Phishing is a type of social engineering in which attackers pose as legitimate entities in order to fool victims into divulging personal information like passwords and credit card details via phony emails, websites, and phone calls.
Malware known as ransomware encrypts a victim’s files and requests a ransom payment in order to decrypt them.
DDoS attacks: These aim to overwhelm a network or website with traffic in order to prevent users from accessing it.
Individuals and organizations should use a multi-layered approach to computer security to safeguard against these and other risks. This comprises:
Using and maintaining antivirus software
being watchful while accessing links from unfamiliar sources or receiving emails
Using strong passwords that are different for every online account
updating operating systems and software with the most recent security patches
frequently backing up crucial data
educating staff members about security threats and how to handle them
It’s also critical to keep up with the most recent developments in cybersecurity risks and trends. This can be accomplished by signing up for security newsletters, following cybersecurity authorities on social media, and going to conferences and events related to cybersecurity.
In conclusion, computer security is crucial for defending against cyberattacks and safeguarding personal and company data. Individuals and organizations can reduce the likelihood of a successful assault by using a multi-layered strategy and keeping up with the most recent threats. Computer security

Computers and security by Omega
For high performance computing (HPC) tasks including simulation, modeling, and data analysis, Omega computers are a type of supercomputer. For activities requiring a lot of computational capacity, these computers are often employed by academic institutions, governmental organizations, and commercial businesses.
The ability of omega computers to process vast amounts of data rapidly and effectively is one of their primary characteristics. They can handle complex calculations more quickly than conventional computers because they have strong processors, lots of memory, and rapid interconnects.
Omega computers provide special security-related difficulties. These systems are frequently used to process delicate data, such as secret government information or confidential corporate data. They must therefore be safeguarded against a variety of dangers, including as cyberattacks, data breaches, and unauthorized access.
There are several ways to protect omega computers, including:
Segmenting the network requires breaking it into smaller subnets, each of which is secured by a different set of security controls. Computer Security This makes it more challenging for an attacker to compromise the entire network and enables more precise access control.
Firewalls: A firewall is a device used to stop unauthorized traffic that is positioned between a network and the internet. This may be a useful strategy for guarding against cyberattacks on the Omega computer.
Even if it is intercepted by an adversary, data can be encrypted to prevent unwanted access. Both data in transit and data at rest may be referred to here.
Access control entails limiting unauthorized users’ access to the Omega computer. A number of techniques, including user authentication and role-based access control, can be used to achieve this.
Regular security audits can be carried out to find weaknesses and potential threats as well as to make sure that security measures are being used as intended.
Omega computers are strong machines built for high performance computing workloads, to sum up. These systems must be protected against a variety of threats due to the sensitive nature of the data they process. Network segmentation, firewalls, encryption, access control, and recurring security audits can all be used to achieve this.
which of the following is true regarding computer security
Because of the growing reliance on technology and the vulnerability of computers and networks to cyberattacks, computer security is a top priority for both individuals and enterprises. Understanding the truth about computer security is crucial as the threat landscape changes constantly.
The fact that computer security is a continuous process is one fact about it. Computer security, in contrast to a one-time installation of security software, necessitates continuous monitoring and updating to stay abreast of emerging threats and vulnerabilities. This include doing security checks, updating software often, and educating staff members on safe online conduct.
There is no such thing as 100 percent security, which is another true statement. Although a computer or network can be protected using a number of security measures, none of the threats can be totally eliminated. This is why it’s crucial to have a thorough security strategy in place that includes several layers of defense and a reaction strategy in case a security breach does happen.
User mistake is one of the major hazards to computer security, which is also a valid statement. Inadvertently clicking on a malicious link, using a password that is too simple, or engaging in other actions could endanger the company’s computer systems. For employees to learn how to recognize and prevent these kinds of dangers, firms must regularly conduct security training.
The possibility of serious repercussions from security breaches is another true assertion. Sensitive data loss, monetary loss, and reputational harm are all possible outcomes of a security breach. For enterprises to quickly contain and lessen the effects of a security compromise, incident response protocols must be in place.

In conclusion, maintaining computer security calls for regular monitoring and updating. Understanding that there is no such thing as 100% security and that user mistake poses one of the major hazards as well as the possibility of serious security breaches is crucial. Organizations must have thorough security plans that cover many levels of defense, frequent personnel security training, and incident response strategies.
dependable computer networks
Data integrity and the protection of sensitive information require secure computer systems. The requirement for secure computer systems is more important than ever because as technology advances, the threat landscape likewise becomes more complex and diverse.
A firewall is one of the essential elements of a secure computer system. A firewall is a hardware or software component that sits in front of a network’s connection to the internet and is made to filter out unauthorized traffic. It serves as a firewall separating the internal network from the outside world and can be set up to permit or block particular types of traffic in accordance with predetermined criteria.
Encryption is a crucial component of a safe computer system. When plaintext is encrypted, it is turned into ciphertext, rendering it unintelligible to those lacking the necessary decryption keys. To stop unwanted access, this can apply to both data in transit and data at rest, including files and databases.
A secure computer system must also have access control. This entails limiting access to the system to only those users who are permitted, and it can be done in a number of ways, including through user authentication and role-based access control. This helps to prevent unauthorized access and data breaches by ensuring that only those who are allowed to access the system may do so.
For secure computer systems, regular security audits are essential. Audits can be carried out to find weaknesses and potential threats as well as to verify that security measures are operating as intended. In order to guarantee that data can be recovered in the event of a security incident, this also includes vulnerability screening, penetration testing, and routine backups.
Additionally, it’s critical to maintain operating systems and applications up to date. Applying security updates and patches as soon as they are accessible can assist to address known vulnerabilities and fend off potential threats.
In conclusion, secure computer systems are crucial for safeguarding confidential data and preserving data integrity. Computer Security Firewalls, encryption, access control, routine security audits, and maintaining current operating and software can all help achieve this. Organizations may defend themselves against a variety of cyberthreats and guarantee the security of their computer systems by putting these measures in place and keeping them up to date on a regular basis.
the most secure computers for cyberspace
The issue of cyber security is crucial for both individuals and businesses. Strong and secure computers are becoming more and more necessary as technology develops. We’ll talk about some of the greatest laptops, desktops, and servers for cyber security in this article.
Let’s start by discussing laptops. A laptop with a strong processor, lots of memory and storage, and a dedicated graphics card is suitable for individuals and small teams. The Dell XPS 13 or 15, MacBook Computer Security Pro, and Lenovo ThinkPad T series are a few excellent choices. These laptops are made of sturdy materials to resist the wear and tear of regular travel and are powerful enough to meet the demands of cyber security software.
A desktop PC with higher power and expandability is a better choice for larger enterprises. For teams working on cyber security, the Dell OptiPlex, HP EliteDesk, and Lenovo ThinkCentre are all excellent choices. These PCs may be quickly upgraded to match the requirements of an expanding firm and offer greater processor, memory, and storage than laptops.
And finally, a server is a need for companies that handle a lot of sensitive data. The HP ProLiant, Lenovo ThinkSystem, and Dell PowerEdge are all top choices for servers used in cyber security. High performance, expandability, and security features like hardware-based encryption and sophisticated authentication are all provided by these servers.
In conclusion, the requirements of the person or business determine which computer is ideal for cyber security. While desktop computers work better for larger firms and servers are necessary for those with a lot of sensitive data, laptops are fantastic for individuals and small teams. Computer Security To protect your data and network from online attacks, buy a computer with a strong CPU, lots of memory and storage, and strong security measures.

the safest computer
There is no one “most secure” choice when it comes to computer security because the necessary level of protection varies on the particular use case and the degree of risk involved. However, some computer and system types have been built with security in mind and have a number of safeguards in place to guard against online dangers.
A computer that is “air-gapped” is one example of a very secure computer. A computer or network that is physically separated from every other network and device is known as a “air-gapped system,” which Computer Security makes it very difficult for an attacker to intrude. These systems are frequently employed in military, government, and critical infrastructure companies where data security is of the utmost significance.
A “hardened” system is an additional illustration Computer Security of a highly secure computer. A computer that has been set up to be more secure than a typical system, typically with the aid of specialist software and hardware, is known as a hardened system. This includes attributes like tamper-proof enclosures, secure boot, and disk encryption. In sectors like finance, healthcare, and government where sensitive data needs to be protected, these systems are frequently employed.
A “crypto-computer” is another kind of extremely secure computer. Specialized equipment called “crypto-computers” is created for the safe processing and storing of cryptographic keys. They frequently have tamper-proof casings and hardware security modules (HSM) that provide extra defense against online and offline threats. These systems are frequently utilized in sectors including finance, government, and other establishments that deal with highly encrypted sensitive data.
Using a machine that runs an open-source operating system is another very secure choice. A sizable developer community contributes to the security of open-source operating systems like Linux by examining the code and discovering vulnerabilities. Additionally, they are thought to be less susceptible to malware than proprietary operating systems.
The need of having a thorough security plan in place, including several layers of defense and frequent security audits, should be noted regardless of the kind of computer system or the level of security. This will make it easier to make sure that the computer systems are safe from a variety of cyberthreats and that vulnerabilities are found and fixed.
Finally, the type of use case and degree of risk involved determine which computer is the most secure. However, choices that are thought to be very secure include air-gapped systems, hardened systems, Computer Security crypto-computers, and open-source operating systems. To ensure their computer systems are safe from a variety of cyber attacks, organizations must also establish a thorough security plan with many layers of defense and frequent security audits.
security for quantum computing
The field of technology known as quantum computing is very young and is now undergoing rapid development. It has the potential to completely alter how we manage and safeguard data. But along with quantum computing’s Computer Security potential advantages come some special security issues that need to be resolved. In this post, we’ll talk about the security of quantum computing as well as the dangers and difficulties it might present.
The possibility of quantum computers breaking encryption techniques that are currently thought to be impenetrable is one of the biggest security issues posed by this technology. This is due to the fact that quantum computers are able to process massive volumes of data at a rate that is significantly quicker than that of ordinary computers, allowing them to factor big prime numbers, the building blocks of many encryption techniques, very quickly. This implies that if a quantum computer were able to crack the encryption, sensitive data that is currently shielded from attacks could become exposed.
Quantum hacking is a further difficulty. Quantum bits, or qubits, are significantly more fragile than conventional bits and are the foundation of quantum computing systems. This makes them more vulnerable to interference and manipulation, making it possible for hackers to gain access to or alter the data kept in a quantum system. In addition, the so-called “quantum side-channel attacks” that take advantage of the characteristics of quantum systems to extract sensitive information can also be used to exploit the vulnerability of quantum systems.
Researchers and businesses are working to create new, more secure encryption algorithms that can fend off quantum attacks in order to address these issues. The development of post-quantum cryptography, a collection of cryptographic methods intended to be secure against both classical and quantum computers, is one illustration of this. In order to safeguard against quantum hacking, businesses are also focusing on designing hardware and software that is quantum-safe.

In conclusion, quantum computing is a potent technology that could fundamentally alter how we manage and secure data. It also presents a particular set of security issues that must be resolved. To defend against quantum attacks, researchers and businesses are presently working on creating new and more secure encryption algorithms as well as quantum-safe gear and software. To safeguard the security and integrity of our data as quantum computing develops further, it is crucial to be educated and proactive.
Dell security for computers
Security is a top priority for Dell, a leading supplier of technology solutions and computer hardware. A range of security solutions from Dell are available to shield networks and computer systems from online dangers.
The Basic Input/Output System (BIOS) security on Dell computers is one of their most important security measures. Dell has put in place a number of security safeguards that serve to protect the BIOS from malicious assaults. The BIOS is a low-level piece of software that regulates the fundamental operations of a computer. There are two of these features: BIOS password protection, which helps prevent unwanted access to the BIOS settings, and secure boot, which makes sure that only reputable software may be loaded during the boot process.
Data encryption is a key component of Dell computer security. Data can be encrypted both in transit and at rest using one of the several encryption solutions provided by Dell, such as Dell Data Protection | Encryption. Even if it is intercepted by an attacker, this aids in Computer Security preventing unauthorized access to sensitive data.
In order to limit access to computer systems and networks, Dell also provides a range of access control solutions. One of these is Dell Secure Auth, a Computer Security multi-factor authentication system that may be used to confirm users’ identities prior to Computer Security granting them access to a system. Additionally, enterprises can manage Computer Security who has access to what resources and how they may access them thanks to Dell’s Identity and Access Management solutions.
Dell additionally offers Dell SafeGuard and Response, an AI-based endpoint security solution that can identify and address attacks on endpoints. Malware protection, vulnerability scanning, and incident response are some of the functions it offers.
Additionally, Dell provides a range of services that might assist businesses in protecting their computer systems. These services, which include security evaluations, penetration testing, and incident response planning, can assist firms in identifying weaknesses and potential threats as well as in creating a strategy for handling security occurrences.
As a major supplier of computer hardware and technological solutions, Dell places a high priority on security. In order to safeguard computer systems and networks from online dangers, Dell provides a number of Computer Security security solutions, such as BIOS security, data encryption, access control, endpoint security, and security services. Organizations may defend themselves against a variety of cyberthreats and guarantee the security of their Dell computer systems by putting these solutions in place and keeping them up to date on a regular basis.
managed services for computer security
Companies that focus on offering businesses and organizations IT security solutions frequently offer managed computer security services. Firewalls, intrusion detection and prevention systems, anti-virus software, and other security measures are frequently included in these services.
The key advantage of managed computer security services is that they enable companies and organizations to delegate their IT security requirements to a group of professionals that have the necessary knowledge and experience to maintain the security of their systems and networks. As a result, companies and organizations can save a lot of time and money because they won’t have to spend it hiring staff and purchasing equipment to operate their own IT security systems.
The peace of mind that comes from knowing that their networks and systems are guarded by a team of professionals who are continually monitoring and updating their security procedures to stay ahead of the most recent threats is another benefit of managed computer security services for businesses and organizations. This can assist companies and organizations in preventing costly data breaches and other security disasters that could seriously harm their reputation and financial situation.
Managed computer security services have another advantage in that they frequently offer businesses and organizations a variety of security solutions that may be customized to meet their unique demands. This can range from fundamental security tools like firewalls and antivirus software to more sophisticated ones like intrusion detection and prevention systems and data encryption.
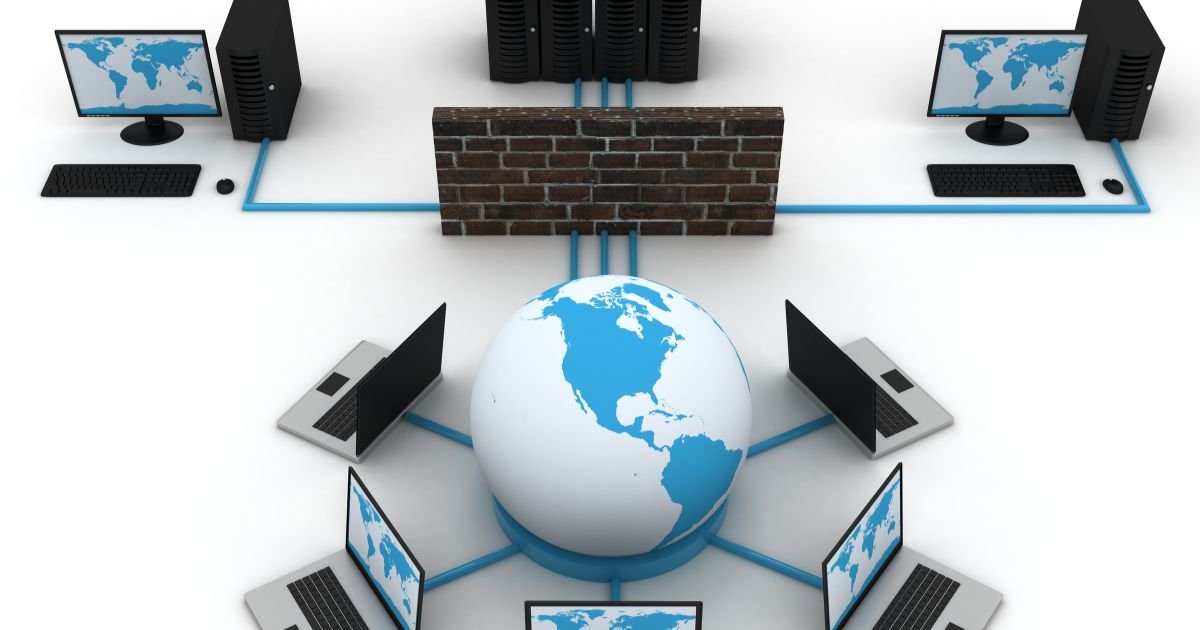
In conclusion, managed computer security services are an economical and effective approach for companies and organizations to maintain the security of their networks and computer systems. They enable businesses and organizations to outsource their IT security requirements to a team of experts who are constantly monitoring and updating their security measures to stay ahead of the most recent threats. They offer a variety of security measures that can be customized to the particular needs of the business.
difficulties with saas security in cloud computing
Users can access and use software programs online thanks to the cloud computing concept known as software as a service (SaaS). Although SaaS might have numerous advantages, like flexibility and cost savings, it also presents new security issues that need to be resolved.
Data security is one of the key SaaS security concerns. Users’ data is stored on servers owned and managed by the SaaS provider because SaaS apps are hosted in the cloud. Risks including illegal access, data breaches, and data loss may result from this. SaaS companies must put in place robust security mechanisms, such encryption, access limits, and frequent security audits, to protect user data in order to reduce these risks.
The sharing of private data is another security concern with SaaS. Multiple users may have access to the same application and data in a SaaS setting. Risks including data breaches, illegal access, and loss of confidentiality may result from this. SaaS providers must have robust Computer Security access controls in place to make sure that only authorized users have access to the data and that it is only shared with those who need to know in order to reduce these risks.
The inability to govern the infrastructure is a third problem. Although consumers have limited visibility and control over the infrastructure, SaaS providers are in charge of keeping the cloud infrastructure that the SaaS application is operating on secure. Because of this, it may be challenging for businesses to evaluate the security of their SaaS apps and to handle security problems. Customers must regularly undertake security audits and testing, and SaaS providers must regularly update their customers on security issues.
The absence of compliance rules is another potential problem. The data kept in SaaS providers’ systems may be subject to compliance rules that they are unaware of, which could result in noncompliance and fines. SaaS providers must adopt the required controls to ensure compliance and be aware of the compliance requirements that apply to their systems in order to mitigate this risk.
In conclusion, SaaS can have a lot of advantages, but it also creates new security issues that need to be resolved. Data security, sharing of sensitive information, a lack of infrastructure control, and a lack of compliance rules are some of these difficulties. SaaS providers must put in place robust security measures and send consumers regular security updates and reports in order to reduce these risks. To protect the security of their SaaS applications, customers must also perform routine security audits and testing.
secure small business computers
Technology is increasingly being used by small businesses to manage their operations and interact with clients. The potential of cyberattacks and other security concerns also increases with this greater reliance on technology. To ensure their sustained success, small firms must take precautions to safeguard their sensitive data and infrastructure.
Implementing fundamental security measures, such as firewalls and anti-virus software, is one of the most crucial things small businesses can do to safeguard their computer systems. These precautions can aid in limiting malware infection and preventing unauthorized access to sensitive information.
Regularly updating their operating systems and software is a crucial action that small businesses can do. This reduces the possibility of a cyber attack and guarantees that any known security flaws are corrected.
Small organizations should also think about adding more sophisticated security measures like intrusion detection and prevention systems, data encryption, and multi-factor authentication in addition to Computer Security these fundamental security measures. These precautions add an additional layer of security and might be particularly crucial for small firms that deal with sensitive client data.
In the event of a security problem, small firms should also have a disaster recovery strategy in place. This strategy should include steps for swiftly restoring any lost data and bringing the system back to regular operation.
Employee education is a crucial component of small business computer security. Small firms should regularly train their staff on optimal security procedures and ensure they are aware of the significance of protecting their systems and sensitive data.
And finally, small companies ought to think about collaborating with a managed security service provider. These service providers can Computer Security provide a variety of security services, such as monitoring and updating security protocols and offering knowledge to assist small businesses in navigating the always evolving world of cyberthreats.
Finally, small enterprises must prioritize computer security. Small firms can protect their sensitive data and systems and assure their ongoing success by putting in place basic and advanced security measures, routine software upgrades, a disaster recovery plan, employee training, and collaborating with a managed security service provider.
Berkeley computer security
The University of California, Berkeley is not an exception to the fact that computer security is a major concern for both individuals and companies. The university has put in place a number of safeguards to defend its networks and computer systems from online threats.
Firewalls are one of the most important aspects of computer security at Berkeley. Firewalls are hardware or software programs that sit in front of a network’s connection to the internet and are made to filter out unauthorized traffic. This aids in defending the university’s computer systems from online threats and unlawful entry.
The use of encryption is a crucial component of computer security at Berkeley. When plaintext is encrypted, it is turned into ciphertext, rendering it unintelligible to those lacking the necessary decryption keys. Even if it is intercepted by an attacker, this aids in preventing unauthorized access to sensitive data. Berkeley employs encryption to protect files, databases, and other data types that are stored at rest and in transit.
Another crucial aspect of Berkeley’s computer security is access control. The institution employs a number of techniques, such as user authentication and role-based access control, to limit access to its computer systems and networks. This aids in ensuring that data is only shared when necessary and that only authorized individuals have access to the systems.
The university also performs security audits on a regular basis to find weaknesses and potential threats. In order to guarantee that data can be recovered in the event of a security incident, this also includes vulnerability screening, penetration testing, and routine backups.
In order to help academics, staff, and students recognize and prevent cyber risks, Berkeley’s IT department also offers security education and training to the campus community. This includes instruction on safe online habits including using strong passwords, avoiding phishing scams, and being aware of what to do in the event of a security crisis.
In conclusion, the University of California, Berkeley places a high priority on computer security. The institution has put in place a number of security measures, including firewalls, encryption, access control, regular security audits, and security training, to safeguard its computer systems and networks from cyber threats. Berkeley can defend itself against a variety of cyberthreats and guarantee the security of its computer systems by putting these steps into place, reviewing them frequently, and updating them.
computer-based security awareness training’s magic quadrant
Gartner, a renowned research and consultancy firm, uses a Magic Quadrant as part of their research approach to assess and rank businesses in a specific industry. A report that assesses and ranks businesses that offer computer-based training (CBT) solutions for security awareness training is called The Magic Quadrant for Security Awareness.
The two primary axes used to evaluate vendors in the Magic Quadrant for Security Awareness CBT are “Ability to Execute” and “Completeness of Vision.” The “Ability to Execute” axis looks at a vendor’s market presence, product capabilities, and overall performance. Computer Security The “Completeness of Vision” axis measures how well a vendor can innovate and adapt to changing market conditions.
Gartner divides vendors into four quadrants based on three factors: “Leaders,” “Challengers,” “Visionaries,” and “Niche Players.” Leaders are companies with a significant market presence and a track record of Computer Security providing high-quality CBT solutions. They also have a distinct vision for the direction the market will take in the future and a strong track record of doing so.
Vendors known as challengers are those with a significant market presence and a track record of providing top-notch CBT solutions. They might not, however, possess the same level of inventiveness and vision as the leaders. Visionaries are suppliers who are at the vanguard of innovation and have a clear vision for the market’s future, but may not have the same level of market presence and execution as the leaders. Vendors known as niche players specialize in a certain market and may not exhibit the same level of market presence or execution as market leaders or challengers.

Organizations intending to deploy CBT solutions for security awareness training may find the Magic Quadrant for Security Awareness CBT to be a useful resource. Organizations can choose which suppliers to Computer Security collaborate with and which solutions to implement by assessing vendors based on their ability to execute and comprehensiveness of vision.
It’s important to remember that the Magic Quadrant only represents the state of the market at a certain time; a vendor’s standing within the Computer Security quadrant may shift over time. To find the best solution for their unique needs, organizations should also perform their own analysis and study.
In conclusion, Gartner uses a research technique called the Magic Quadrant for Security Awareness Computer-Based Training to assess and rank businesses that offer CBT solutions for security awareness training. Computer Security The report divides vendors into four categories—Leaders, Challengers, Visionaries, and Niche Players—based on how well they can carry out their plans and how comprehensively they do so. The Magic Quadrant can be a helpful resource for businesses looking to implement CBT solutions for security awareness training, but it’s important to keep in mind that it only represents a market at a particular time, so it’s crucial to carry out your own analysis and research to find the best option for your needs.
A guide to cloud computing security needs
Protecting sensitive data and systems from illegal access, breaches, and other cyber threats requires strong cloud computing security. We’ll outline the security needs for cloud computing in this post, along with best practices for setting up and maintaining a secure cloud environment.
Access Control: Access control is one of the primary security requirements for cloud computing. To ensure that only authorized users may access sensitive data and systems, this includes managing user authentication and authorization as well as putting multi-factor authentication (MFA) into place.
Data Encryption: Data encryption is a crucial component of cloud computing security. To prevent unwanted access and breaches, all sensitive data should be encrypted both in transit and at rest.
Network Security: Network security is also essential for cloud computing because it aids in defending against online dangers like malware and DoS assaults. To stop unwanted access to the network, this may entail putting in place firewalls and other security measures.
Compliance: When using cloud computing services, particular compliance regulations from many organizations must be complied with. HIPAA for healthcare enterprises, PCI-DSS for companies that process credit card payments, and SOC 2 for SaaS providers are a few examples of this.
Regular security audits and testing can assist organizations in identifying vulnerabilities and potential threats so that action can be taken before they are exploited. Regular penetration testing, vulnerability scanning, and security evaluations fall under this category.
Incident Response and Business Continuity Plan: Having a plan in place for incident response and business continuity is crucial for responding to security incidents promptly and recovering from them. Detecting and reporting security breaches, as well as putting in place procedures for data recovery and business continuity, are a few examples of what this can include.
Implementing these security measures can assist firms in defending against unwanted access, data breaches, and other online dangers to sensitive data and systems. To keep up with the changing threat landscape, it is critical for enterprises to periodically examine their security procedures and change them as necessary. Organizations should also think about collaborating with a cloud security vendor who can assist with setting up and managing these security policies.
controls for cloud computing security
In recent years, cloud computing has grown in popularity as more businesses realize its numerous advantages, including cost savings and scalability. However, security is a key risk with any technology. Organizations adopting cloud computing must install a range of security procedures in order to safeguard their data and systems.
Access control is one of the most crucial security measures for cloud computing. This entails limiting access to the cloud environment to only authorized users, and it can be done in a number of ways, including through multi-factor authentication and role-based access control. This assists in preventing unauthorized access and data breaches by ensuring that only users who are allowed to access the system may do so.
Data encryption is another crucial security measure. In order to prevent unwanted parties from accessing the data, unencrypted data must be transformed into ciphertext that is impossible to decipher. To stop unwanted access, this can apply to both data in transit and data at rest, including files and databases.
Network security is a third security measure. Organizations should make sure that firewalls, intrusion detection and prevention systems, and other network security tools are in place to safeguard their cloud environment. This aids in defending the cloud environment against hacker attacks and unlawful entry.
Response and management to incidents are another crucial security measure. In order to ensure that security incidents, such as data breaches, are handled quickly and effectively, organizations should have a plan in place for how to respond to such situations.
Cloud security also requires routine security audits and compliance assessments. To find potential vulnerabilities and threats, organizations should perform frequent security assessments, vulnerability scans, and penetration tests. Additionally, they must make sure that they are abiding by all applicable laws and standards, including SOC 2, HIPAA, and PCI-DSS.
Security is a major issue while using cloud computing, to sum up. To safeguard their data and systems, organizations must adopt a range of security measures, including access control, data encryption, network security, incident response, incident management, routine security audits, and compliance checks. Organizations may defend themselves against a variety of cyberthreats and guarantee the security of their cloud environment by putting these measures in place, reviewing them frequently, and updating them.
utilizing the cloud for cyber security
The usage of cloud computing by businesses of all kinds for a variety of tasks, such as data storage, software development, and cybersecurity, has grown in recent years. In this post, we’ll examine cloud computing’s place in cybersecurity and how it might be used to ward off online dangers.
Data Backup and Recovery: The simplicity of data backup and recovery is one of the most important advantages of cloud computing for cybersecurity. Organizations may make sure they can access their data even in the case of a disaster or security incident by keeping it on the cloud.
Scalability is another benefit of cloud computing for cybersecurity. Organizations may have to use more resources to defend against cyber threats as they become more sophisticated. Organizations can rapidly and effectively scale up their cybersecurity capabilities using cloud computing as needed.
Security solutions offered via the cloud: Numerous cybersecurity options are now offered via the cloud. Threat intelligence, intrusion detection, and vulnerability management are all included. Organizations can benefit from the newest technologies and keep abreast of the most recent dangers by utilizing cloud-based security solutions.
Compliance: The use of the cloud can assist businesses in adhering to numerous cybersecurity laws. Organizations can make sure they comply with the relevant regulations, for instance, by utilizing a cloud-based security solution that is HIPAA or PCI-DSS compliant.
Cost-effectiveness: Compared to conventional cybersecurity solutions, cloud computing may be more affordable. Organizations can save money on the cost of hardware, software, and maintenance by employing cloud-based services.
Accessibility: Cloud computing makes it easier for security professionals to monitor systems and respond to security problems since they can access their data and tools from any location with an internet connection.
It’s crucial to remember that while cloud computing might improve cybersecurity, it also presents a unique set of security issues. Organizations must make sure that the cloud providers they use have appropriate access controls and are secure and compliant. To keep up with the changing threat landscape, security controls must be continually reviewed and updated.
Finally, cloud computing has become a crucial component of contemporary cybersecurity. It enables businesses to simply backup and recover data, scale up their cybersecurity capabilities as necessary, and benefit from the most recent technological advancements. Organizations must, however, make sure that the cloud providers they use are safe, compliant, and have the right access restrictions in place.
policy for securing cloud computing
When employing cloud computing services, enterprises must adhere to a set of rules and processes known as a cloud computing security policy. When utilizing cloud computing, it is crucial for enterprises to have a thorough security strategy in place as it can help to defend against a variety of cyber threats and guarantee the security of the organization’s data and systems.
Access control is one of the most important elements of a cloud computing security policy. Through a number of techniques, including multi-factor authentication and role-based access control, access control is the process of limiting access to the cloud environment to only authorized users. This assists in preventing unauthorized access and data breaches by ensuring that only users who are allowed to access the system may do so.
Data encryption is a crucial part of a cloud computing security policy. Data encryption includes transforming plaintext data into ciphertext that is impossible for unauthorized parties to decipher. To stop unwanted access, this can apply to both data in transit and data at rest, including files and databases.
Network security is the third element of a cloud computing security policy. Organizations should make sure that firewalls, intrusion detection and prevention systems, and other network security tools are in place to safeguard their cloud environment. This aids in defending the cloud environment against hacker attacks and unlawful entry.

Incident management and response are crucial components of a security policy for cloud computing. In order to ensure that security incidents, such as data breaches, are handled quickly and effectively, organizations should have a plan in place for how to respond to such situations.
A cloud computing security policy must also include regular security audits and compliance checks. To find potential vulnerabilities and threats, organizations should perform frequent security assessments, vulnerability scans, and penetration tests. They must also make sure they are following the rules.
Read More: Computer Security